Document Security in the Age of Cyber Threats
Why has document security become a concern?
Documents have become one of the weaknesses in modern cybersecurity. Contracts, financial reports, records of employee personal data, drafts, and medical records, they all are files.
Before, when everything was printed on paper and locked in a safe or a cabinet, it was way safer than today. However, in a digital landscape, each PDF file or scanned copy is a potential entry point for criminals.
So the approach to document security is no longer just a niche for the IT industry. It's something that matters for every business, every manager, and even a freelancer. We will talk about this in our article, considering why this situation is happening and what we can do about it.
The evolution of cyber threats
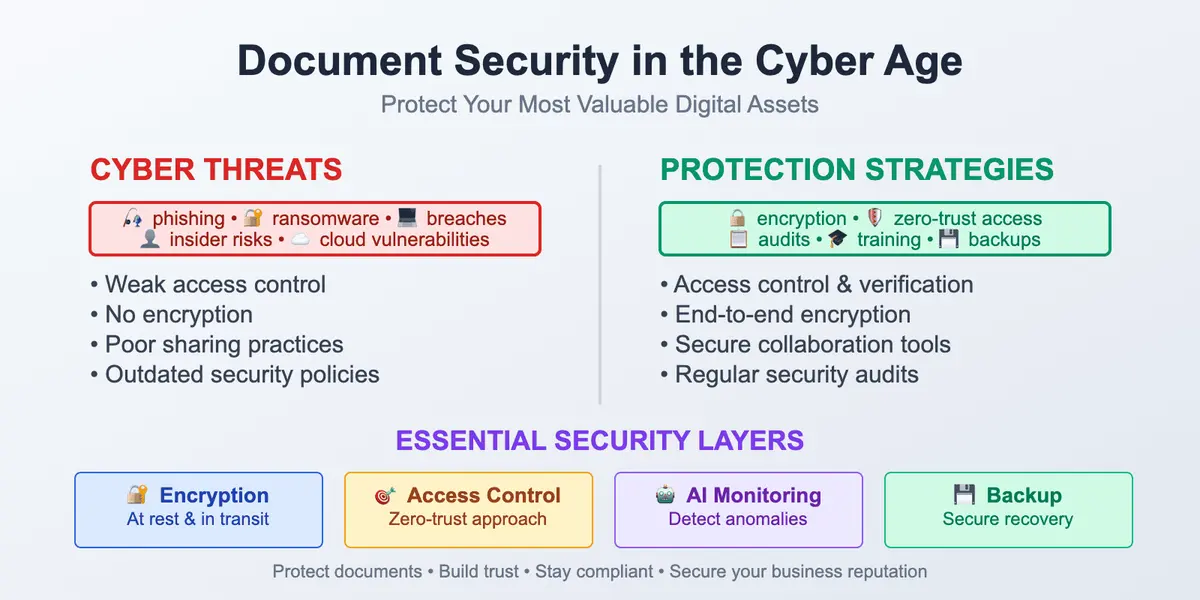
The landscape of threats, which are really dangerous for digital documents, has been growing exponentially since the very first digital files went online. It's not just about one attacker trying to break into a system. It's about organized criminal groups, well-trained hackers, and even corrupted state-sponsored players. Here are some milestones and important parts of this evolution:
1. Phishing
Many attacks start not with breaking code, but with understanding human psychology. For example, a single email with an attachment that looks trusted can be enough to ruin an entire system and even an entire company.
2. Encrypting files (ransomware)
Criminals who specialize in breaking cybersecurity can encrypt your files, including sensitive documents, and then demand payment from you to unlock them.
3. Employee risks
Sometimes the danger comes from insider threats, because employees don't realise that they are violating safety rules and end up leaking data or mishandling documents. This can happen either intentionally or simply due to poor training.
4. Cloud vulnerabilities
Google Drive, Dropbox, and other cloud storage seem very trusted and safe, but at the same time, they carry risks if access to this storage isn't properly controlled.
5. Improper document redaction
When sensitive information is only visually hidden and not permanently removed, attackers can still extract hidden data, resulting in unintended exposure.
The most important point here is that documents are in the centre of attention. They are the objects that hold sensitive information and value. And wherever there is value, there will always be someone trying to steal it.
Why is information so valuable?
Documents become the new vulnerable part of any workflow, especially when they are digital. And if you analyse cyber incidents, especially the most damaging ones, you will realise they are not always about the direct stealing of money, but they are always about stolen information.
For example, an agreement that can influence current stock prices, a medical record that can destroy the reputation of a patient, the draft of some contracts that cost millions and contain commercial secrets, and so on.
That's why many experts say documents are the new jewels in the crown of any organization. If you lose control over them, you will lose much more than files, because it's about credibility, it's about reputation, and sometimes it's about your entire business. To prevent such risks, many companies now automate document redaction in their workflows to protect sensitive information before it's exposed.
The main weaknesses in document security
Most companies and businesses don't fail at document security because they consider it very important and use a smart approach and advanced systems. But they can fail because of such gaps that they don't consider risks. They include:
Weak access control
Too many people have access to files they don't really need and don't really relate to. It's a problem because human error is one of the weakest parts of any system.
No encryption
Documents are stored or sent in plain text, which is very easy to intercept.
Poor sharing practices
Sensitive information in files is shared over email without any protection.
Lack of training
Employees in companies don't know how to recognise and fight risks. They don't understand the safety policies in the company, and they don't understand what integrity really means.
Outdated policies
Security rules written five years ago don't match reality because the digital landscape is changing very quickly. You need to update policies at least once every half a year.
The sad truth is that hackers often don't need to be super geniuses or super professional. They just need to find the weakest part in your system, for example, in your document management and workflow. In fact, those weak parts are everywhere.
How to protect documents effectively
What does it mean to apply working methods of document protection, especially in the modern world where cyber threats are everywhere? One must understand that it's not about installing some software and considering it enough. No, it's about creating a system and a culture within the company that will help to protect information and sensitive content in your documents. Using secure document management just means keeping your files organized and protected so only the right people can access them. This approach helps ensure that files are treated as secured documents throughout their entire lifecycle.
Here are the core principles:
- Access control and the zero-trust concept. Only people who need specific documents must have access to them. The zero trust concept assumes that no user or device is automatically safe, and everyone undergoes strict verification every time.
- Encryption everywhere. Each process in a workflow must be encrypted. All documents should always be unreadable to anyone who doesn't have access. Encryption may sound like a complex methodology, but today it's very often built into existing software, so you just need to switch it on.
- Secure collaboration. Remote workers will stay part of each process in almost every company, so it's important to send attachments using secure platforms with built-in permission controls. That must include link expiration dates for storage files, watermarks, and so on.
- Regular audits. You don't just think that your security policies are working and don't need updates. Audit documents, access logs, check who's downloaded what, and identify unusual and suspicious patterns.
- Training and awareness. All employees must be aware of existing safety policies in a company. They must undergo training on how to deal with phishing attempts and how to use secure document sharing tools.
- Backup and recovery. Even if your system is hit by a phishing attack, a clean backup will save it. But backups must also be secured, tested, and audited.
- Automation and monitoring. To keep documents secure in 2026 one must combine manual control with automated security tools. Tracking document activity in real time and simultaneous detection of anomalies allows responding to potential system threats effectively.
Which document storage model is safer?
There are two main models that help to prevent leaks and keep documents secure. Some believe that keeping documents in-house gives more control and minimises risks, and others think that cloud storage providers have better security, they know more about safety, and they also spend more budget on security than most companies. But in fact, both concepts have specific risks and must be considered in the broader context of data security and established document security best practices.
- Storing documents in-house means that it's very important to monitor them 24/7, which is almost impossible for companies. Internal IT practices must be on a very high level, which is also one of the weak parts, and the hardware updates must be provided continuously.
- Risks related to cloud storage are issues with permission configurations, the need for the company to rely on a third party, and exposure to mass breaches, which is also a risk.
The key is not choosing one or the other model. The key is configuring whichever system you use properly and being able to manage it.
The rise of automated document protection
A lot is changing with AI and automation that are starting to play a role in document security.
- Automatic redaction tools scan documents and black out sensitive details before sharing. They are game changers.
- Data loss prevention allows systems to detect when someone tries to send sensitive documents outside the safe network.
- Behaviour monitoring with AI can see unusual patterns, changes of access, and user activity.
Our automated document redaction software powered by AI does not replace human involvement in control, but they reduce the chance of mistakes, which is very important when it comes to document safety and data protection.
Balancing security with usability
There is one big potential issue in document security. If you make it very strict, people can't access the documents they need for work. And, of course, they may start looking for shortcuts. That leads to using personal emails, USB drives, and so on. That violates the safety policies of almost any company.
The challenge is to protect documents without sacrificing the productivity of your team. The best security policies feel almost invisible to the user, and they are easy to deal with. They protect but don't require completing too many steps for every action from an employee.
Small actions that make a big difference
Not every company has millions to spend on cybersecurity, but even small teams can take smart steps. They include:
- Using strong passwords and enabling two-factor authentication;
- Storing documents in encrypted drives or clouds;
- Limiting file sharing via email, using secure links;
- Regular review and audit of who has access to what;
- Keeping systems updated.
Security doesn't have to be expensive, but it has to be systematic.
Conclusion
Document security is an ongoing process for each company which treasures their workflow, reputation, and even existence. Even if the tools and methods may change in the future, it's important to protect information according to the current trends. Partners, employees and clients trust you with their details, and losing the trust once means that it may never come back.
As cyber threats continue to evolve, staying proactive and consistently improving how documents are protected is no longer optional, but essential.
Whether you are running a huge multinational company or just a freelancer with a laptop, you must treat your documents as if they are the most precious things you have, because they really are in our digital age. Stay secure!