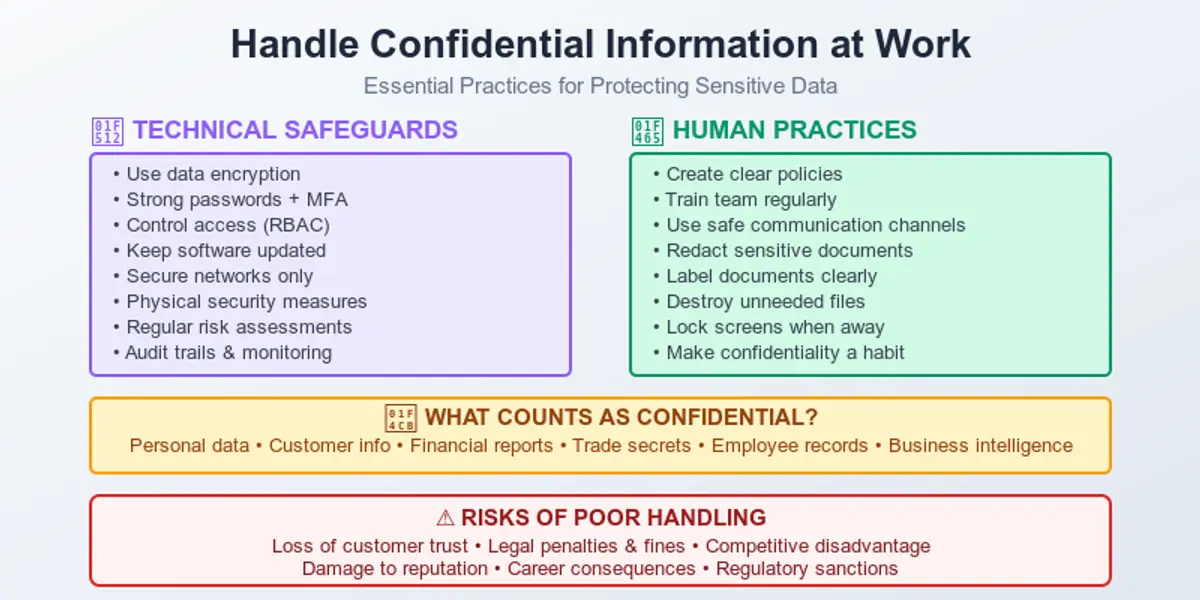
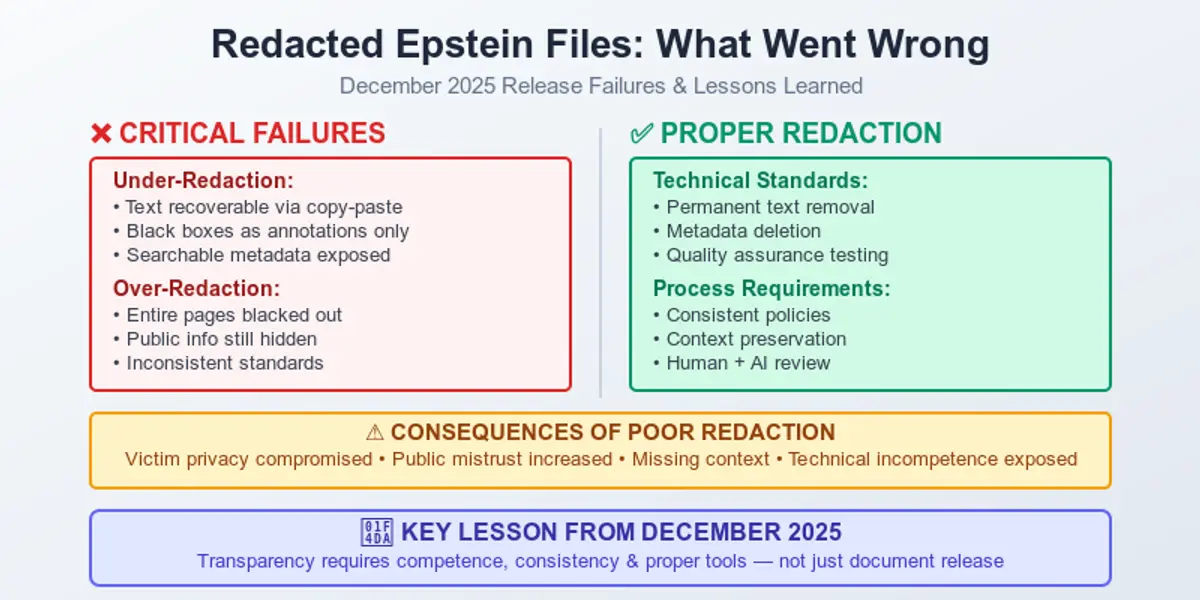
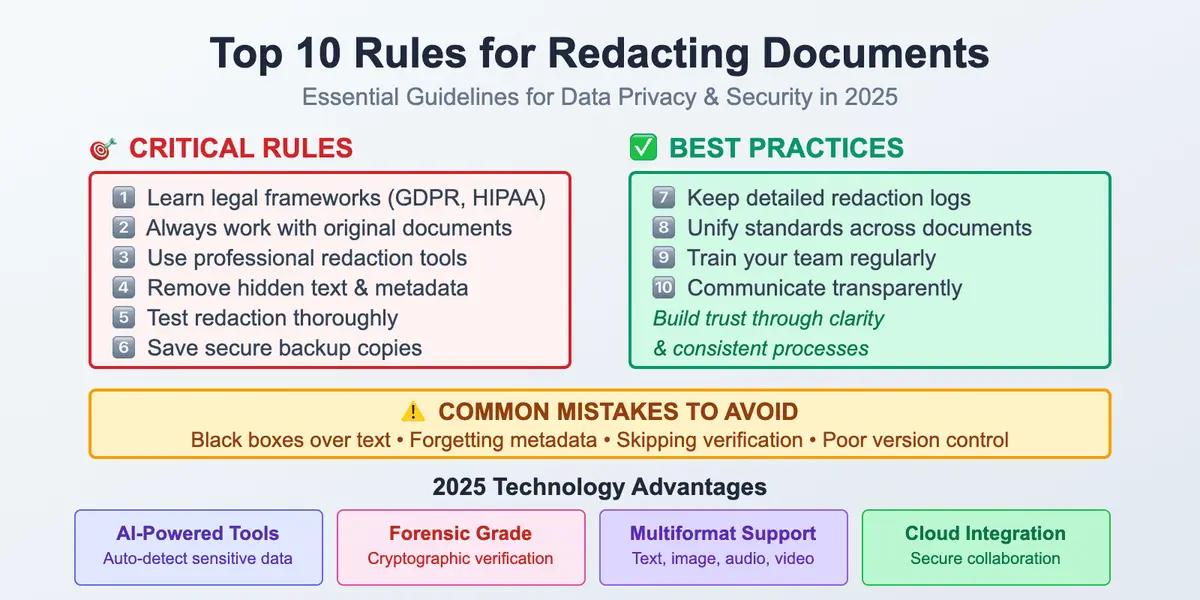
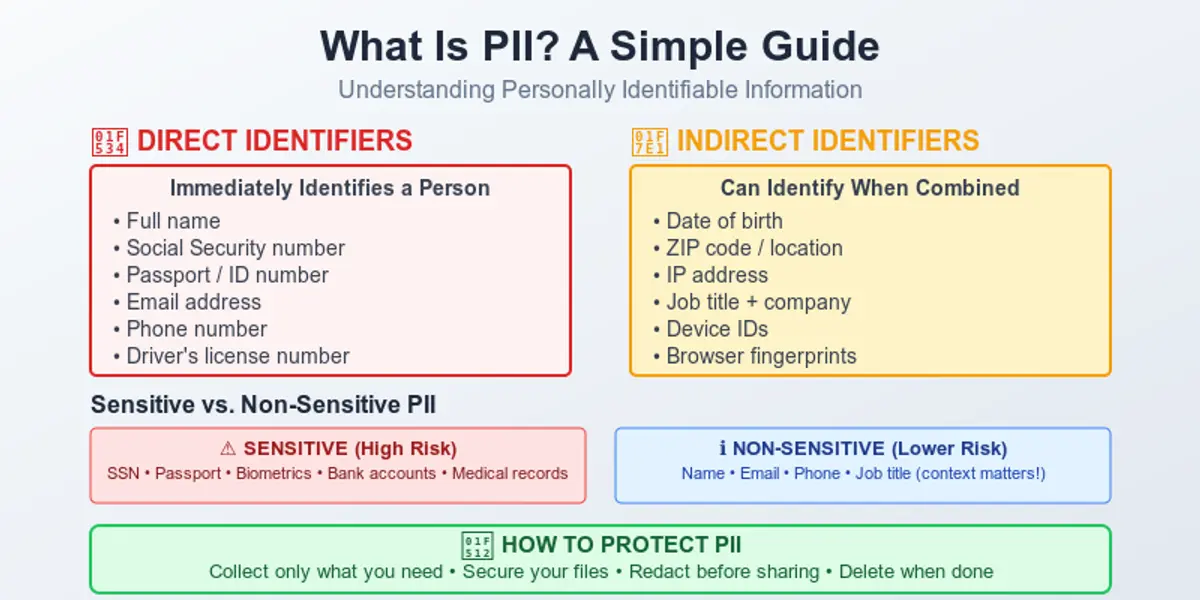
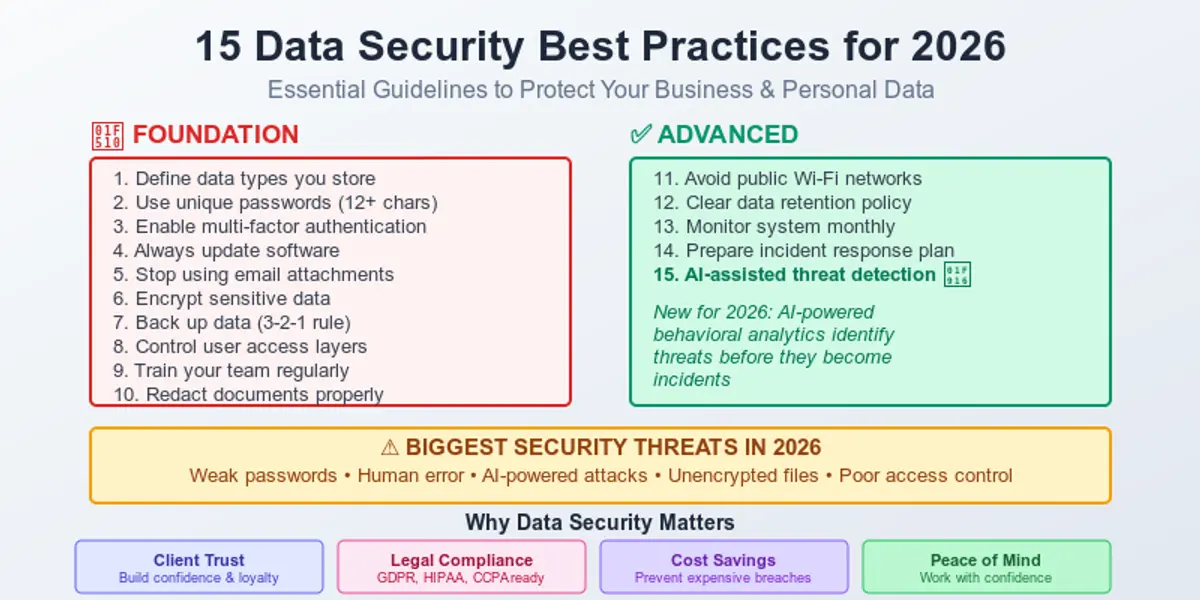
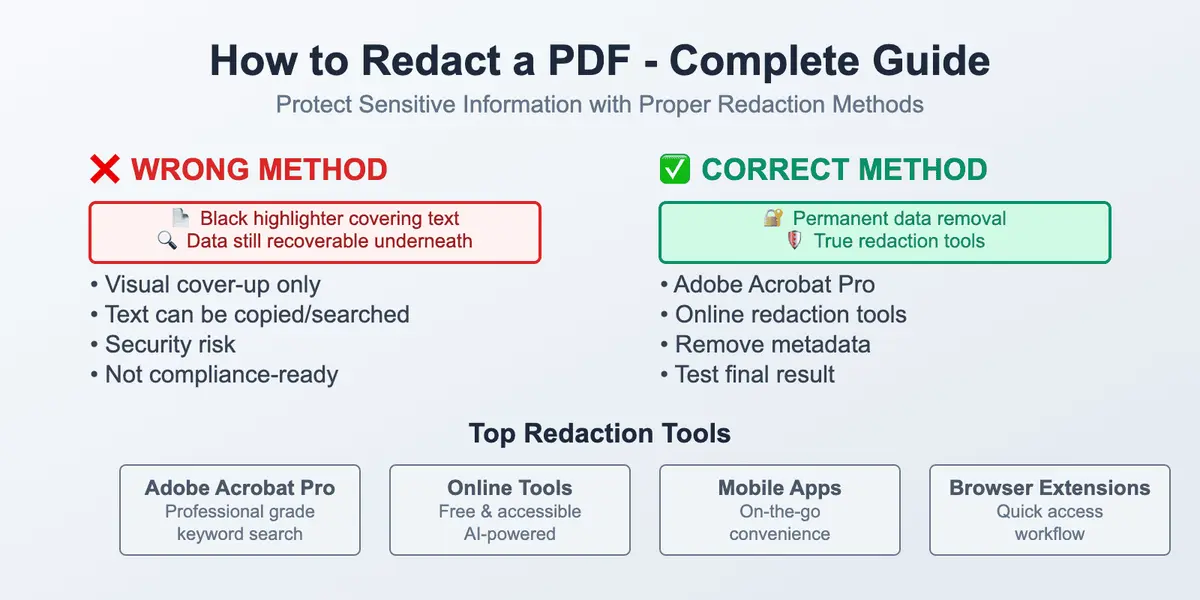
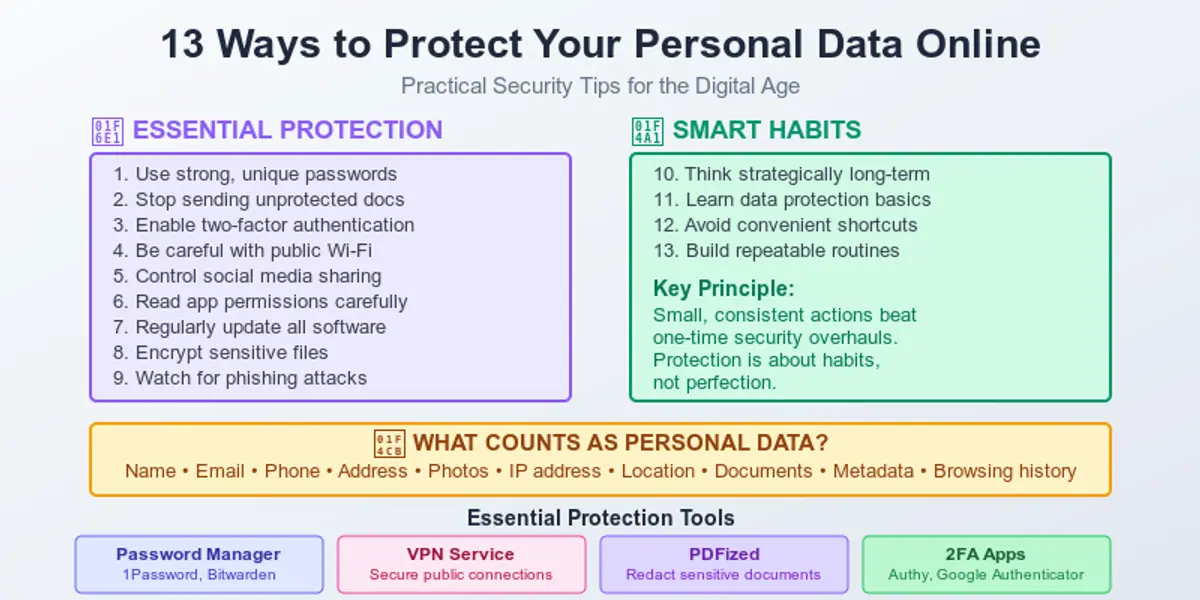
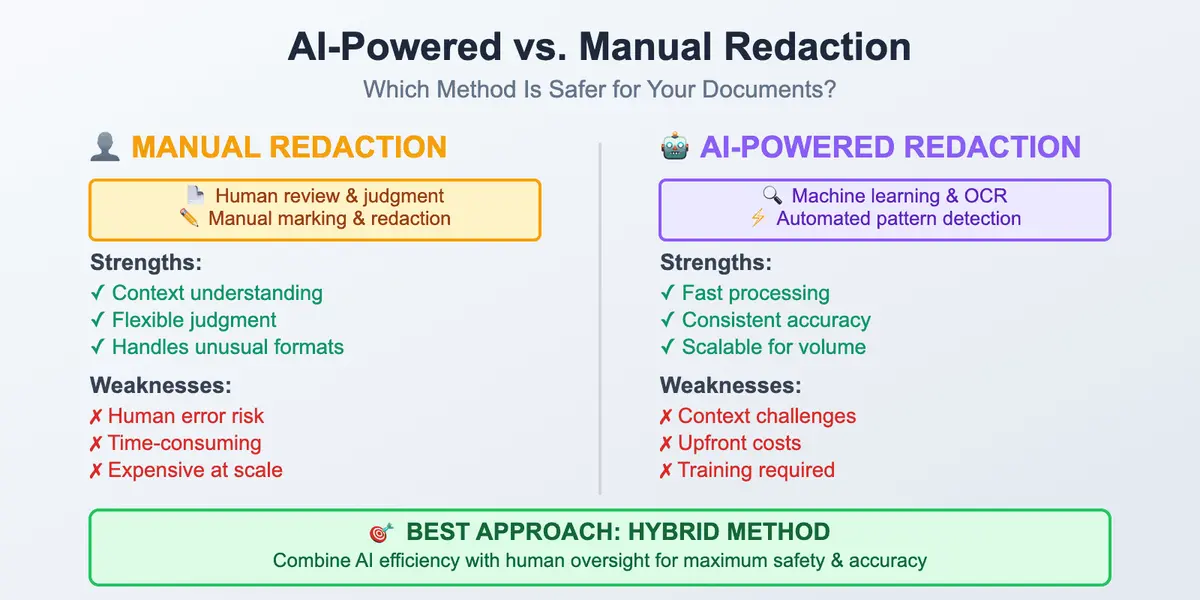
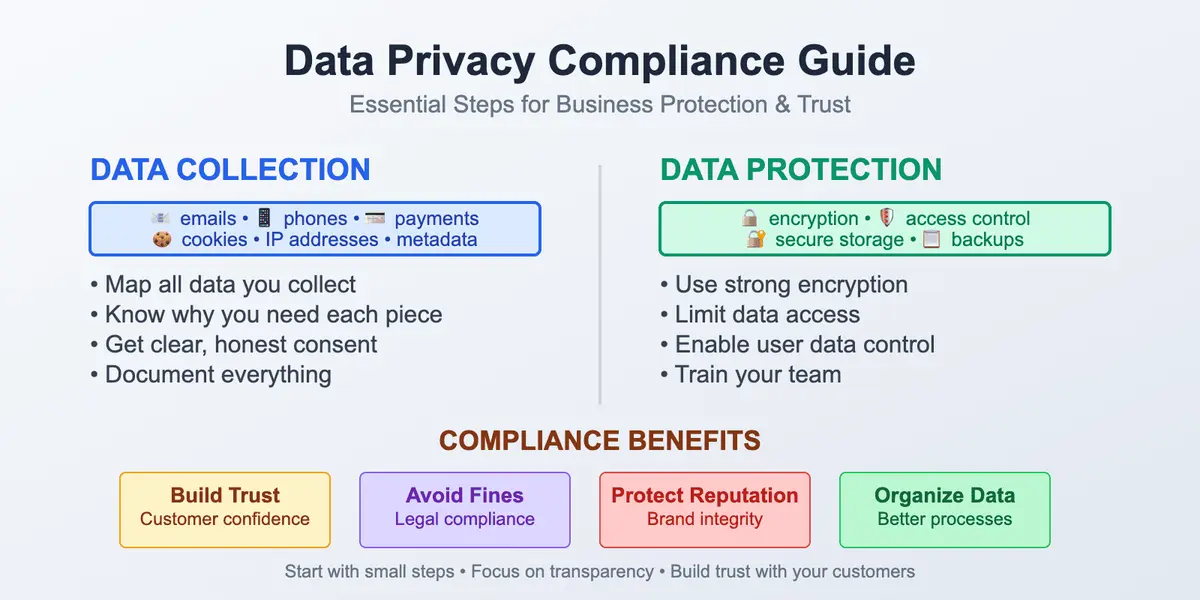
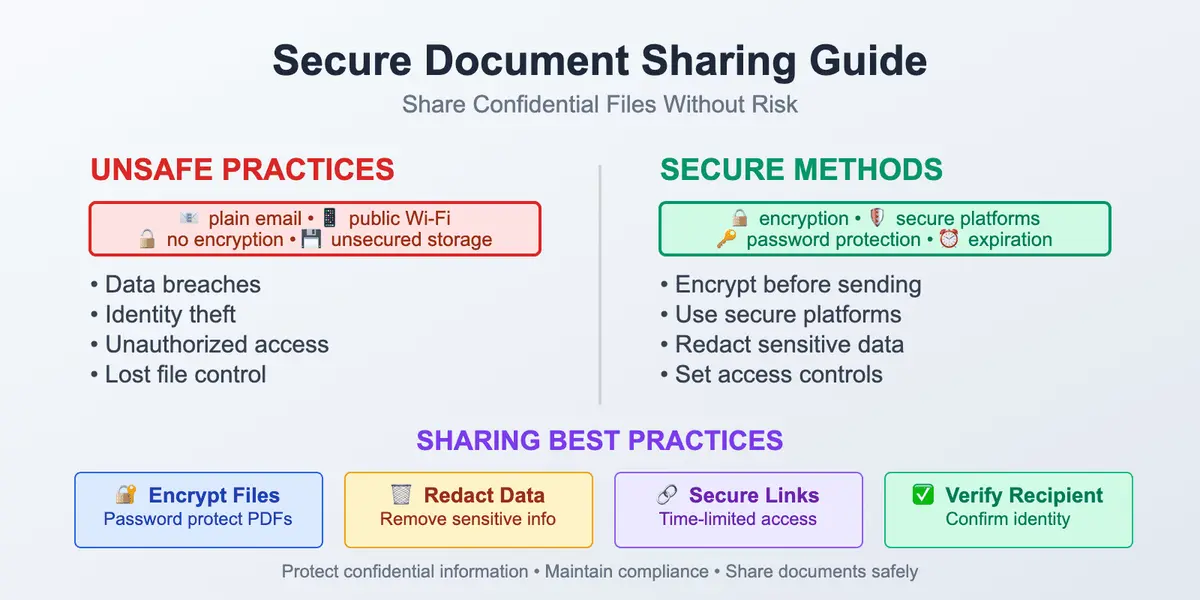
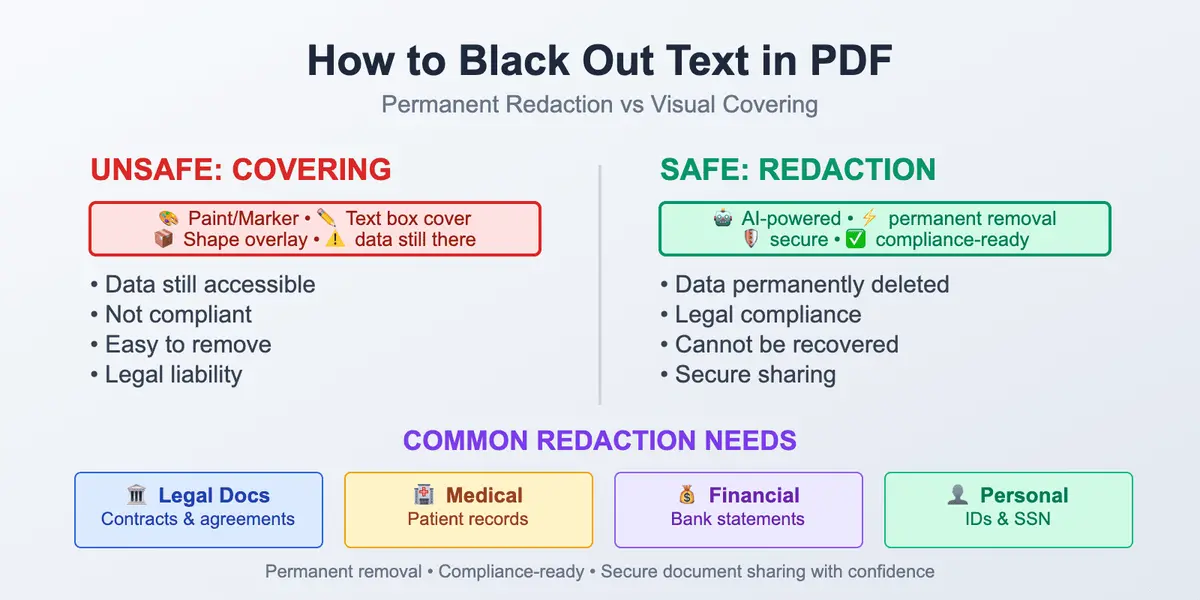
The world we live in instantly collects information about us. That’s why having a practical, human-level guide on how to stay safe in such a situation is a must. Understanding how to protect your personal data online is no longer optional – it’s a basic skill in everyday digital life. It may sound unnecessary or boring, but it all lasts only until the moment it suddenly becomes real. Safeguarding personal information has become essential in everyday digital life, with so much data being shared and stored online.
For example, a hacked email or a leaked document. You may be surprised and shocked, but someone can use your photos, your ID, address, or private messages without your permission. Even a file you casually sent to a friend may show up where it absolutely shouldn’t. It’s not magic, it's the reality of hackers’ activities.
Most people don’t think about data protection because nothing bad has happened to them yet. That’s exactly how risks start to grow. Invisibly and quietly, long before the consequences appear, they can change the whole situation dramatically.
In this article, we will help you become more proactive and aware of the main cybersecurity risks. After reading it, you will better understand how to survive in the modern world with all its digital threats. We will talk about practical, realistic ways to protect your personal data online in a way that actually fits real-life situations.