Data Security Best Practices: A Friendly Guide for 2026
Nowadays, data security isn’t something only for big companies or people who work in the IT industry. Today, it’s the center of every digital action one takes, from sending emails, booking clients, communicating with your team, storing documents, and so on.
If you’re a freelancer, a small business owner, a manager who works with sensitive client details, or if you simply use your laptop or iPhone daily, data security is your job.
The good news is that this process doesn’t have to be problematic or stressful.
Technically, when you break data security down into clear habits, it becomes a natural part of your workflow. Just like you check your emails daily.
Our guide will provide you with information about the best data security practices for 2026.
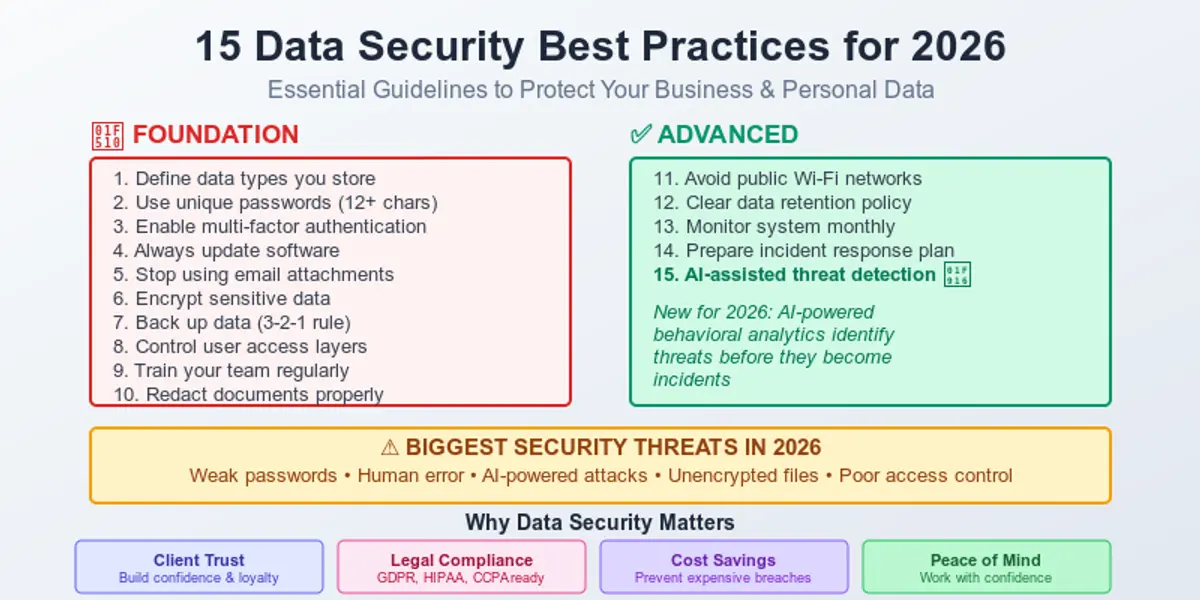
1. Define the types of data you have and store
At the very beginning, you need to understand what types of data you’re going to protect. You have to start with the revision of everything that exists in your storage. Because most security problems begin because business owners don’t realize how much sensitive data they actually have, or where they store them.
You need to define what types of data you collect from clients, and where this sensitive data is stored and protected. For example, it can be stored as attachments in emails, or you may use cloud storage. Also, you need to understand who from your company has access to this data, and how long you keep documents that contain sensitive information.
After such a revision, you will realize that you have a lot of data you do not have to store anymore. For example, old client contracts, passport scans from the pricing sheets, financial documentation, and so on.
So, after you finish, you need to have a clear list with information about all data you store, and where you store it, as well as who can access it.
2. Use unique passwords
On one hand, almost all people today realize that a strong password is a must for anyone, either for an individual or for a person who works in a corporation.
But at the same time, most security issues still happen because someone just hacked the system because of a weak password. Some passwords are still not protecting systems, repeated or cliché words and phrases, rows of numbers, and so on.
If you want to protect your data with a strong password, you need to follow several rules:
- The password must be at least twelve characters;
- A password must contain uppercase, lowercase, numbers and symbols;
- A password must not contain personal details of a holder;
- The same password must not be used on different platforms;
- Using a password manager is a must.
3. Multi-factor authentication everywhere
Enabling MFA is a great idea if you want to keep your data safe. Multi-factor authentication adds another layer to your protection system, so it will be very hard for someone to enter your storage, even if they will hack your password. MFA is good for:
- Emails;
- Cloud storages;
- Financial accounts;
- Communication apps;
- Project management tools;
- CRM systems.
4. Always update your software
You regularly see notifications from different apps about the update, and most people just think that it’s possible to do later.
However, many of the updates include improvements that relate to security, because any system can contain vulnerabilities. That’s why developers constantly work on improving systems, and when they ask you to download and install the updates, they do it for your sake.
You regularly have to update:
- Laptops;
- Phones;
- Operating systems;
- Apps;
- Browsers;
- Website plugins;
- Cloud tools.
Make it a habit to stay protected.
5. Forget about email attachments
For many it could seem surprising, but email attachments is a very risky format of storage files, because forwarding emails too many times may lead to loss of information or leak of information. It’s very easy to intercept an email attachment. It’s not protected.
If you want to enclose some files, you have to share documents properly. It's better to use secure file sharing links and access controlled cloud storages. You must send attachments compressing them into a ZIP file, protecting them with a password.
6. Encrypt sensitive data
If you have never tried implementing encryption to your workflow, it may seem complicated, but it’s a quite simple concept.
Both data in transit and at store are marked with unreadable codes that only can be unlocked with the specific key. Encryption will turn your documents invisible to anyone except you.
7. Back up your data
It’s very important to back up and it’s crucial not only for storing files and not losing them.
In terms of data security, backup is about having a strategy against hacking attacks as well as accidental deletion of files.
The best back up strategy contains three layers:
- You need three total copies of your data;
- You need two different storage types, for example, a cloud storage and file sharing storage;
- One stored offline in a physical device.
8. Control user access
One of the biggest security threats when it comes to teams is that it’s possible for anyone to access files. This may lead to a mess up, to accidental deletions, to confusions, to unnecessary exposure and so on.
So in the company it’s crucial to have several access layers for employees that will include different control types. For some it will be limited and for some it will be read-only and only administrators will have the full control over documents.
Also remember that if someone leaves your team you need to remove their access to any files.
9. Train your team
Human error is one of the main factors that cause data leaks. Even if you’re a freelancer and don’t have any other people in your team, you need to understand how document security works. So you must focus on team training and teach them to:
- Recognize phishing emails;
- Secure password habits;
- Safely handle client documents;
- Update software;
- Report suspicious activity;
- Use secure file sharing methods;
- Make security a culture of your company.
10. Redact documents properly
Use professional and trusted document redaction tools and implement this action as a habit in your team.
Most people think that just placing a black square over text in a PDF means that it hides the information but in reality it doesn’t work like that because such information can still be copied and pasted, extracted and removed.
Redaction means permanently taking away sensitive information from documents. It’s impossible to recover data after this action. A proper redaction with tools tools like PDFized guarantees that:
- The underlying text in your PDF will be securely deleted;
- Sensitive fragments cannot be restored;
- Metadata is deleted;
- Only the redacted version remains.
This is important for contracts, invoices, passports, NDAs, medical data, client documents and other sensitive data.
11. Do not use public Wi-Fi
If you want to stay safe, use only secure Wi-Fi and never do sensitive work on public networks, because anyone can potentially access your traffic.
To stay safe, you can use a personal hotspot from your phone and a VPN. Ensure that you work only on trusted, password-protected networks and disable autoconnect to public Wi-Fi.
12. Have a clear data retention policy
You don’t have to store all data forever. The more you store, the more you must protect, and it takes away a lot of resources as well as exaggerates risks.
Manage data according to type
If you want to create a working and effective system of data protection in your workflow, you need to:
- Store contracts up to five years;
- Keep payment confirmations up to one year;
- Delete passport scans after the event when they are no longer needed;
- Archive and back up photos;
- Remove client details and clean emails regularly.
The main rule is that you and all employees in your company must know what to keep and what to delete.
13. Monitor your system
You need to add some obligatory actions to your routine. For example, implement regular monitoring of your systems and workflow.
Monthly checks must include:
- Access control;
- Removing unused accounts;
- Detection of suspicious activity;
- Login attempts;
- Checking software updates;
- Backing up everything you need;
- Checking all permissions.
14. Prepare a plan B
Even the best, safest system in the world with properly encrypted files doesn’t give you 100% safety, and incidents may happen. If a problem occurs, you need to know how to react. It’s very important to know the algorithm of actions in case of emergency:
- People who must be notified;
- What access must be restricted immediately;
- How to secure all the documents in the leave mode;
- Passport reset rules;
- Further communication with team and clients.
This plan will give you clarity when something goes wrong.
15. AI-assisted threat detection
Earliest versions of digital security tools can’t deal with modern cyber threats anymore. Using AI-based technologies allows organizations to identify suspicious elements and reduce issues connected with system security. The combination of behavioral analytics and machine learning helps track activity and anticipate potential attacks. When integrated into a security system, AI-assisted monitoring helps identify and reduce potential defense weaknesses. This approach also helps reduce the need for constant manual monitoring, allowing analysts to focus on higher-level tasks.
Conclusion
You need to realize that security is not a burden. It’s a system that actually gives you freedom and economizes your resources.
All the practices we gave you in our article, when implemented, will help you beat anxiety, stop worrying, and feel deep trust in your team and your workflow as a freelancer or business owner. This clarity will free a lot of energy so you can work faster, and your clients will feel it as well.
At the end of the day, data security is about consistency, professionalism, and confidence. If you implement all the steps one by one, even within several weeks, you will feel more organized and secure. Good luck!