How to Protect Your Personal Data Online
The world we live in instantly collects information about us. That’s why having a practical, human-level guide on how to stay safe in such a situation is a must. Understanding how to protect your personal data online is no longer optional – it’s a basic skill in everyday digital life. It may sound unnecessary or boring, but it all lasts only until the moment it suddenly becomes real. Safeguarding personal information has become essential in everyday digital life, with so much data being shared and stored online.
For example, a hacked email or a leaked document. You may be surprised and shocked, but someone can use your photos, your ID, address, or private messages without your permission. Even a file you casually sent to a friend may show up where it absolutely shouldn’t. It’s not magic, it's the reality of hackers’ activities.
Most people don’t think about data protection because nothing bad has happened to them yet. That’s exactly how risks start to grow. Invisibly and quietly, long before the consequences appear, they can change the whole situation dramatically.
In this article, we will help you become more proactive and aware of the main cybersecurity risks. After reading it, you will better understand how to survive in the modern world with all its digital threats. We will talk about practical, realistic ways to protect your personal data online in a way that actually fits real-life situations.
What Does ‘Personal Data’ Mean?
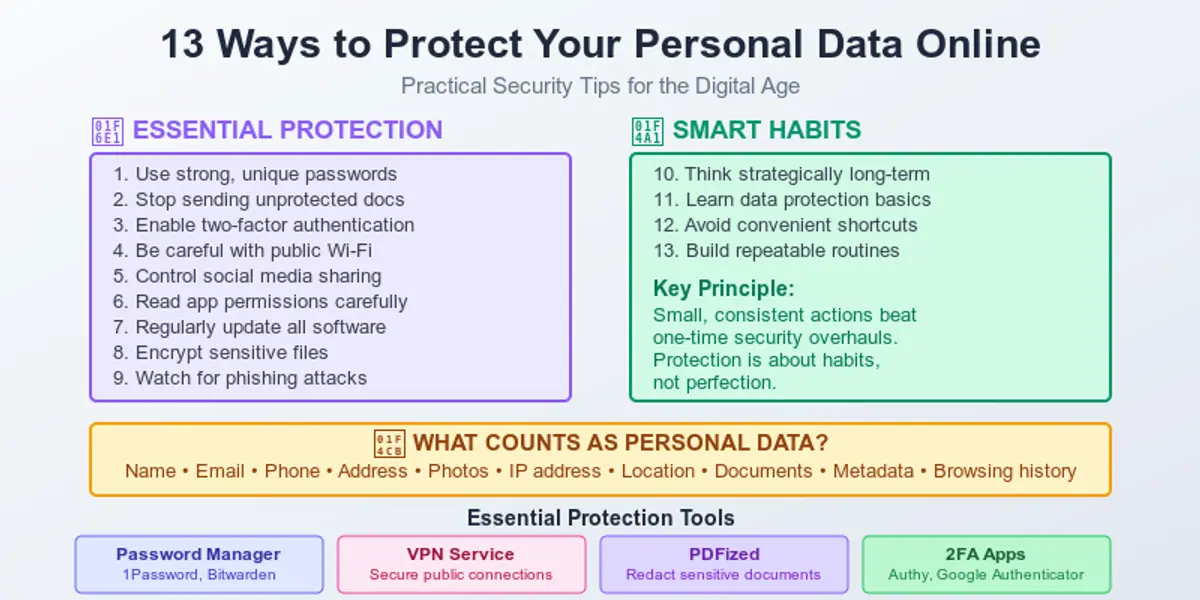
First, you need to understand what personal data really means, because it’s more than you may think. People who hear the words personal data often think about physical objects like credit cards or ID numbers. But that’s only one part of this term. In reality, much of this information is considered PII (Personally Identifiable Information) – details that can be used to identify you, either directly or indirectly, and should be protected.
Your personal data includes:
- your full name, nickname, or username
- email address and phone number
- home and work address
- photos
- IP address and device identifiers
- location data
- documents, PDFs, and contracts
- social media activity
- metadata
- browsing history, and more.
Even something as simple as a scanned document with your name and signature can be enough to identify you. Understanding this is the first step to protecting your personal data. You need to realize how much information about you is already spread online.
15 Practical Ways to Protect Personal Data Online
Here are working ways to protect information you don’t want to share publicly:
1. Use strong and unique passwords
Everyone knows that using one password on several different platforms is a bad idea, but most people still do it. Reusing passwords is one of the easiest ways to lose your accounts. Attackers and hackers can exploit this very quickly.
You need to build several simple but effective habits:
- use unique, strong passwords for different accounts
- make your passwords long
- use a password manager instead of relying on memory
Remember, a strong password doesn’t have to be impossible to remember or very clever. It just needs to be impossible to guess.
And if you’re still using the same password for your email, cloud storage, social media, and other services, you are multiplying your risks significantly.
2. Stop sending unprotected documents
People often send contracts via email, upload PDFs to cloud services, share scanned IDs, forward documents, post screenshots without redaction. One unprotected document can expose names, addresses, signatures, phone numbers, ID numbers, metadata, and sometimes this creates a very serious risk.
That’s why redaction becomes a critical part of personal data protection if you do any activities online. Before sharing any document, you need to ask yourself: ‘What could be used against me if this file becomes public?’
Remember that manual redaction isn't the best way to secure sensitive data. If you want to protect your files, you should use professional redaction tools like PDFized, which automatically detect and redact sensitive information before you share documents.
3. Use two-factor authentication (2FA)
Use two-factor authentication. It may seem unnecessary or like an extra step, but two-factor authentication (2FA) adds an important layer to your data protection system. Usually, it uses a code, app confirmation, or biometric check.
Of course, sometimes it may seem like too much, but it’s absolutely worth it. When someone somehow gets your password, this system can stop them from moving further.
You should use two-factor authentication for:
- email accounts
- cloud storage
- social media
- banking services
- any platform storing personal documents
4. Be careful with public Wi-Fi
Public Wi-Fi networks are risky. If you often visit cafés, airports, hotels, co-working spaces, and similar places, you need to be aware that many of them use unsecured networks, and your data is unsafe there.
If you upload or download documents on public Wi-Fi or send personal information and identifiers, you need to consider safer alternatives. For example, using a VPN or waiting until you get on a trusted connection.
5. Control what you share on social media
Social media can become a big risk factor for people who tend to share a lot. Photos with faces, locations, habits, relationships, schedules, and similar details can expose much more than it seems at first glance.
Even old posts can be used in unexpected ways.
Review your old photos and posts, remove visible addresses, documents, or IDs, check your privacy settings, and limit who can see your content. You need to minimize unnecessary exposure wherever possible.
6. Read permissions on websites and apps
Many applications and websites often ask for access they don’t really need. For example, you may visit a website to download a game, and it asks for your location, even though it doesn’t need it at all.
Before you click the Allow button, make sure it makes sense. And if it doesn’t, deny access.
7. Regularly update your software
Updates on your devices aren’t just about new features. Very often, they fix security bugs, and outdated software is always a risk factor.
Make sure to update:
- operating systems
- browsers
- document viewers
- PDF editors
- cloud apps
Use automatic updates to control this process and avoid forgetting about it.
8. Encrypt sensitive files
Learn more about what sensitive data is to realize that all sensitive information you store needs to be protected with encryption. This applies to hard drives, external storage, sensitive PDFs, backups, and more. Even basic encryption adds a strong layer of protection that many people completely skip. Don’t repeat this mistake.
9. Be careful with unknown links and phishing
Be careful with unknown links. Phishing attacks are very widespread, and you need to be especially careful with emails and links. It’s very easy to get your data stolen just by clicking the wrong link.
Phishing attacks target human behavior, not the level of software protection. That’s why even people with good technical security can still become victims.
You need to pay attention to:
- unexpected attachments
- links that don’t look right
- requests for personal information
- urgent calls to action
Never open documents or click links if you’re unsure about the sender. If you have doubts, it’s better not to touch it at all.
10. Think strategically and long-term
Data protection is not only about one action today. You need to think long-term and ask yourself questions about every file you share.
For example:
- Will this information still be relevant in several years?
- Who might access this file later?
- Could this information be misused in a different context?
Many data leaks cause harm long after the original moment of sharing. That’s why protecting your data is also about doing something good for your future self.
11. Learn more about data protection
Educating yourself doesn’t mean becoming a cybersecurity expert. But you do need to understand basic concepts such as:
- what metadata is
- how PDFs store information
- how tracking works
- how phishing works
- why redaction matters
The more you know, the less afraid you become. Awareness always reduces unnecessary panic and increases control.
12. Avoid shortcuts and choose wisely
Very often, people choose shortcuts because they want to save time. Auto-logins, saved passwords, public uploads, quick shares without checks all of this feels convenient. It’s not always a bad idea. But it shouldn’t be an automatic habit.
Protecting personal data online is about choosing wisely and understanding when convenience is worth the risk and when it isn’t.
13. Build repeatable habits
The best protection is not one big action. It’s a system built from small, repeatable habits.
For example:
- check documents before sending
- redact sensitive information
- use two-factor authentication
- update software regularly
- think before sharing any files.
Consistency matters much more than perfection.
14. Minimize the data you keep
The less information you keep the lower the risk of data exposure. Collecting data without clear purpose isn’t an option if you aim to prevent risks of leaks. To stay safe you should provide regular data reviews, remove old files, track backups and archives. Remove anything that no longer serves legal or business purposes.
15. Verify before you share
Take it as a rule that before sharing any file you should ensure what’s inside this document and who will receive it. Send files only to recipients who really need those data, redact files properly before sharing, and check access permissions. Verifying files before sending them is the easiest way to prevent long-term consequences and leaks.
The Future of Personal Data Protection
The future of personal data protection will be much more complex than it is today, because technologies are developing very fast. Information about people collected by different devices is growing every day. That’s why document security will become more important than ever in everyday digital life. Personal information protection plays a key role in keeping people safe online as digital tools collect and use more sensitive data.
AI, automation, digital services, and so on make our lives much easier. But at the same time, they make us deal with new risks.
Personal data protection will no longer be only about strong passwords or security settings in applications. It will be more about awareness, using smart tools, and behaving proactively.
People will need solutions that work automatically. Reducing human mistakes will be in the center, especially when it comes to documents, files, and data sharing.
Automated redaction and privacy approaches will play a bigger role than they do now. In the future, protecting personal data will not be a technical skill for professionals only. It will be a basic habit for everyone.
Conclusion
Personal data protection is, first of all, about self-respect. It’s not about hiding information. It’s about respecting your own privacy and boundaries.
The digital world is not an easy environment to be active in, and you don’t have to share your information with every platform and every app.
With tools like PDFized, you can be proactive and automate the process of redacting documents, which is a huge step toward better data protection. Our redaction software will help you stay in control, reduce unnecessary exposure of personal data, and protect sensitive information.